Everything is insecure and you’re one bad decision away from being p0wn3d harder than you ever have in your entire life.

It’s a harsh reality and one you’ve got to accept in full or ignore altogether.
I’m from the group that believes we can fix some of the things that are broken, even if only slightly making things better.
So I started doing what I do best: write code.
Learning Python
I’ve had a few reasons to start learning Python, from my interest in Machine Learning and LLMs to pentesting, red teaming, and hacking in general.
I don’t want to build a calculator, todo app, or snake game.
So instead of just reading books and doing a bunch of tasks I wouldn’t be interested in, I jumped head first into hacking scripts.
I dissected a bunch, searched Google, asked ChatGPT questions and eventually cobbled together some scripts that I’m finding useful as I focus more on security for myself and others.
This post showcases a few scripts that I’ve built which could be useful for more people than just me, and I want to share them with you.
Feel free to download, alter and use these codes however you see fit.
Open Source FTW 🤘💯
Combine TXT files
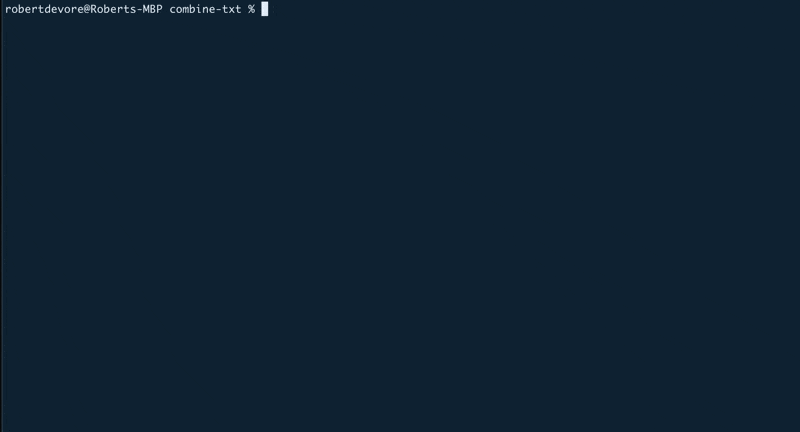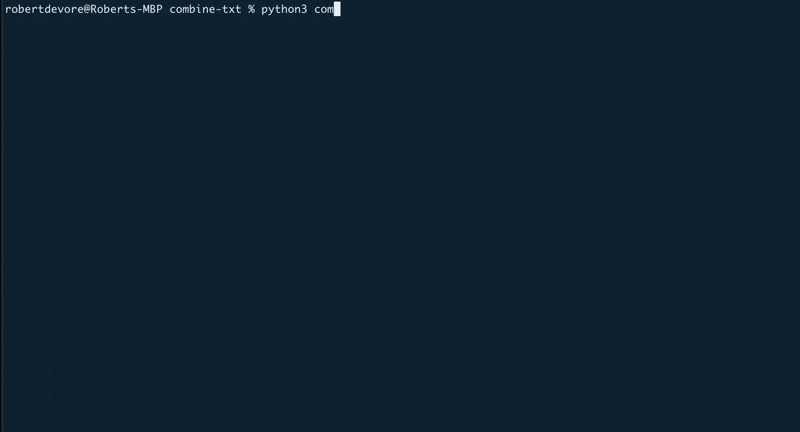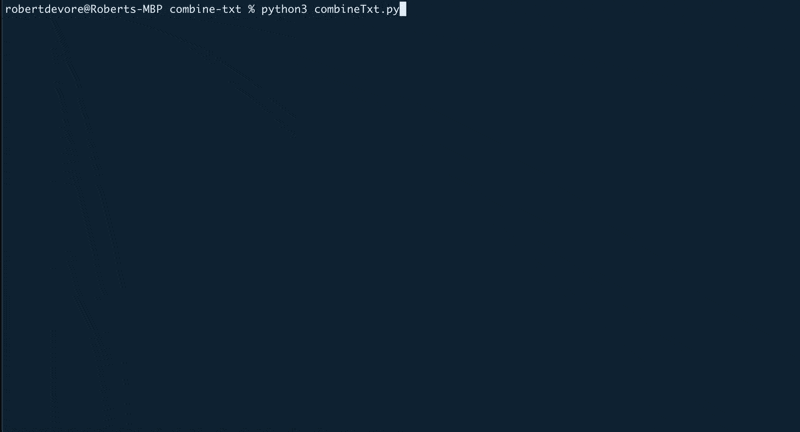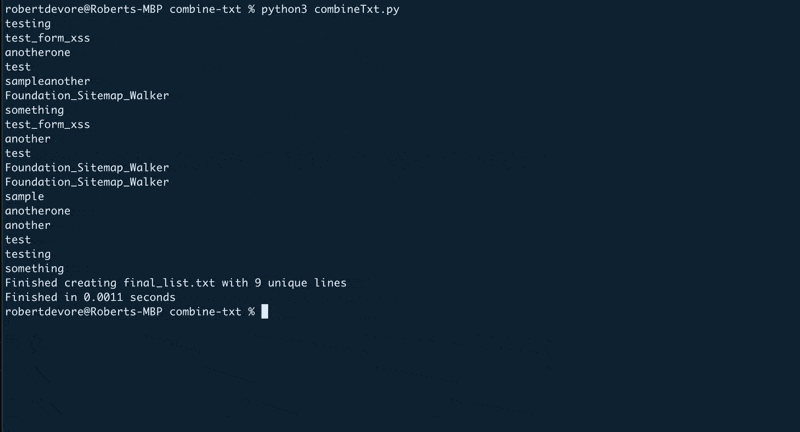
When you’re downloading multiple TXT files full of potential passwords or other data, there’s gonna come a time when you need to combine them into one easy to manage file.
I mean, if you’re building a password cracker (more on that below), you’re not really gonna want to run the same cracker script on dozens of files separately.
That’s where the combine-txt script comes in 😎
Run this script in a folder with multiple
txt
files and it will combine them all, remove duplicates and save the updated list to a new
txt
file.
Email Scraper
When doing recon on a website, you’ll inevitably start gathering as much personal info about the target as possible, including any email address you can find.
So of course I had to create a custom script that would scan domains for any email addresses within the content
The email-scraper script will take a domain name and searches the site for any email addresses, and then stores them in a newly created
txt
file for your review.
Password Cracker(s)
For the times when you are able to gain access to a database of user logins, you can take the hashes you find and try to crack them.
In order to not be a script kiddie (eww, who wants that?), I created a couple of password crackers.
The first one, password-cracker, is a more basic cracker that accepts an md5 hash and runs it against
txt
files to try and find a match.
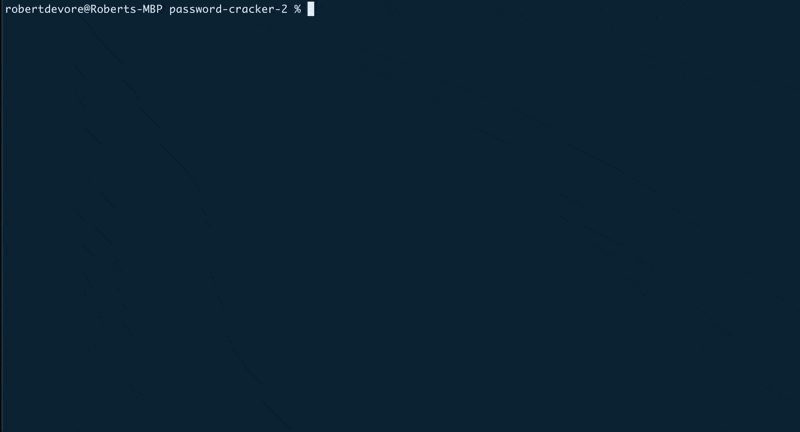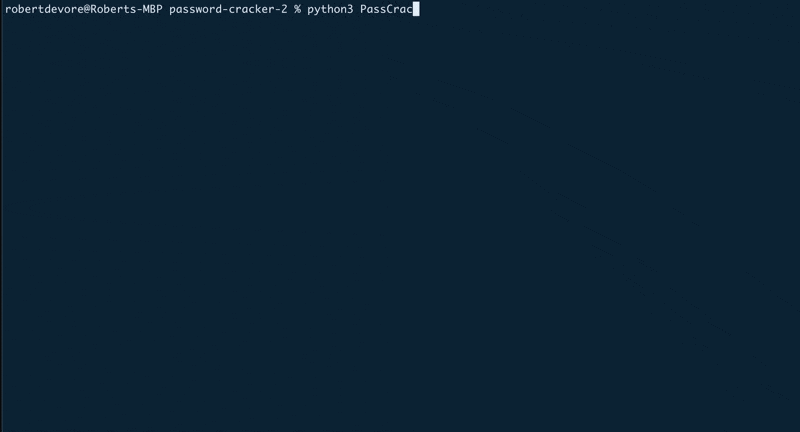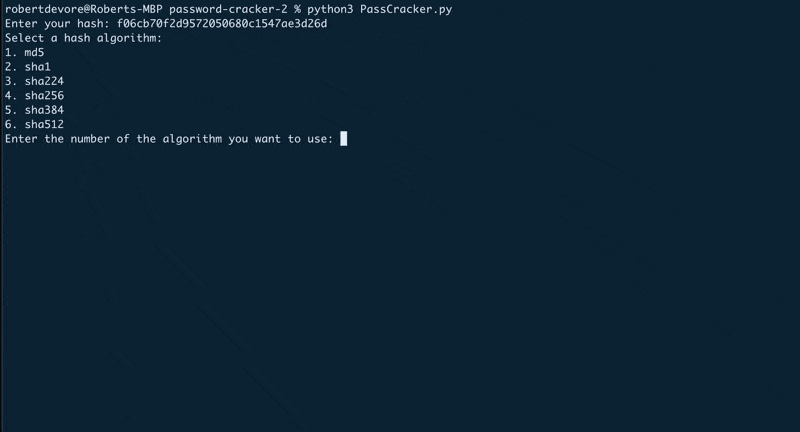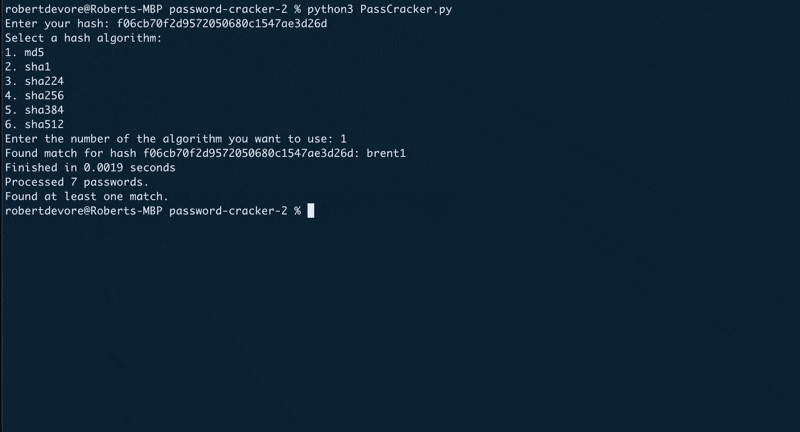
The second one, password-cracker-2, is more robust and one that I plan to continue working on.
That one allows you to provide a hash and also choose which hash you’re trying to crack (md5, sha1, sha512, etc).
Regex Scanner
For the times when scanning through a WordPress site for potential vulnerabilities seems like a daunting task, this script should help speed up that process.
I created the regex-scanner script to help automate the process of searching through theme/plugin/core files in a WordPress site.
The original goal was to find certain types of code that are typically found when a site is hacked.
Things like: eval, fopen, file_get_contents, extract, etc are searched for, but I also added in some outdated PHP code like create_function in order to help with PHP compatibility testing.

XSS Scanner
Continuing with the vulnerability scanning scripts, I decided to build out a suite of scanners for things like XSS, CSRF, etc.
First up was XSS, since it’s one of the lowest-hanging fruit.
The xss-yes script accepts an XML file URL and then scans every URL found inside of it for an XSS vulnerability.

What’s next?
I’m working on building more tools and will continue to release open-source security scripts.
I would like to eventually package a handful of these scripts into one giant tool that can run all of these together, instead of having a ton of individual scripts.
We’ll get there eventually but for now, more baby steps 😎
Leave a Reply